How to Choose Accounts Receivable Automation Software
Featured Resource

Blogs, guides, case studies, interviews, how-tos, expert insights and more—all designed to transform your accounts receivable.

Learn the ins and outs of payment processing and how to create better payment experiences for your customers.
Extend the system you rely on to make AR tasks a breeze.
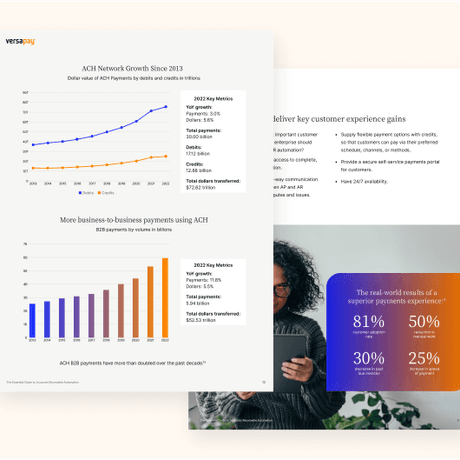
Learn how today's AR automation accelerates cash flow, cuts down on manual work, and delivers better customer experiences.
Empower the genius of teams with this one-of-a-kind approach to AR.
In-depth resources covering everything from finance basics to the latest in new accounting standards.
Get the best stories, insights, and AR best practices delivered to your inbox every month.
Take our 6-minute assessment and learn exactly where you are in your digital AR journey, how you stack up against peers, and how to set your AR team up for success. We'll:













Tips to help you process payments like a pro and keep cash flowing.

We cover everything B2B sellers (and buyers) could want to know about virtual credit cards
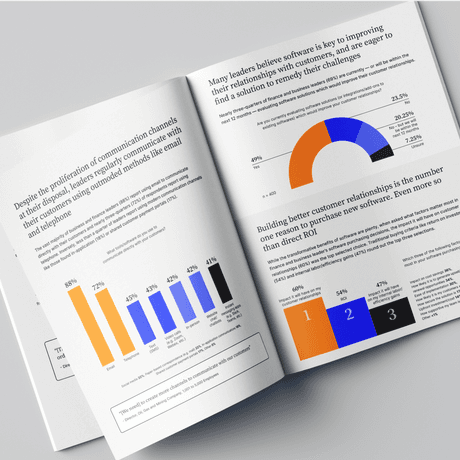
Identify and interpret the data that really counts.
Learn about the practices and technologies that help you ensure every payment matches an open receivable.
Tips, techniques, and practices to get paid what you're owed.